Rohid said that “we really focus on banks, financial institutions and fintech businesses and along with it the cyber security threats to financial systems, we work with leading cyber security solution providers around the world to make finance and public sector specific cyber security programs.”
So what are our findings?
DoS (Disk Operating System), System intrusion and social engineering are the big three attack patterns. At latest report on the Verizon with attacks globally the threats landscape and the biggest so far is denial of services attack, the second largers is system intrusion that’s meanly ransomware and the third one which is really emerging right now are social engineering attack.
System intrusion and social engineering attacks are high risk even though likelihood of basic web attacks is the highest, so here we see, when somebody reports a breach, what percentage after breach is successful in data disclosure. So, it means that if somebody is hacks these systems what is the probability of somebody in the data hackers dealing or up-dealing access to the assessor to the data.
The most wait that people gain accesses is till true basic web applications attack, that means just gassing passwords on cracking password. That very simple stuff. But social engineering and system intrusion have the highest true risk, because your not gonna get basic web application attack which is stealing password from sophisticated and administrated. The possibility of damage is the high on the right down risk from system intrusion and social engineering attacks, because you’re the possibility of killing at administrate access.
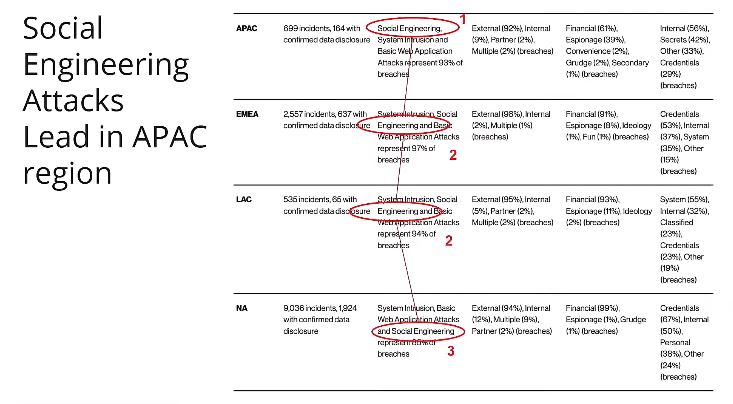
Interestingly that it changes by geography. Social engineering attacks is number one in Asia Pasific, number two in York and Latin Amerika and number three in North Amerika. So in Asia Pasific we’re very careful with the social engineering attacks because it’s really increasing a lot.
Anatomy of a successful attack:
- Initial access : social engineering/basic web application/system intrusion ny exploiting vulnerability.
- Discovery : days spend on network/cloud discovery; accounts (privilege escalation), reachable, network services, permission groups, infrastructure and storage buckets.
- Lateral and vertical movement : use commonly used protocols RDP, SSH and SMB etc to mive through the network/cloud. Explore privilege opportunities as they gain access to resources.
- Defence Evasion : use commonly used protocols RDP, SSH and SMB etc to move through the network/cloud.
- Data Collection : Local systems, internal information repositories such as code repositories, SharePoint, environment files and databases.
- Impact : ransomware attack, data breach and harvesting. Financial, reputational, operational costs.
Rohid said that “one very troubling thing that we noticed is what we called BEC attacks, BEC based attacks have markedly increased owing to their effectiveness, specially well social engineered ones.” He said in the One Data Indonesia & eGOV 2023 websummit, day two, at the Grand Mercure Hotel Jakarta, Thursday (06/07).
According to Europol, “pretending to be consultants, they persuaded the Chief Financial Officer (CFO) to transfer millions of euros abroad. In total, they defrauded the company of almost EUR 38 million in a matter of days.”
Authorities brak up gang responsible for EUR 38 million CEO fraud. A joint investigation supported by Europol has led to the dismantling of a Franco-Israeli criminal gang involved in large-scale CEO fraud (also known ad BEC scams). The operational activities resulted in five action days, which took place between January 2022 and January 2023 in France and Israel. No but seriously this takes weeks of monitoring as well.
Biggest organizational challenge to cyber security programs is:
- Lack of joint business-IT program to address cyber threats. Management lacks visibility and risk perception of cyber threats, so typically in the IT department still with cyber security business teams deal with business things and these no joint teams.
- Inadequate processes; specially use of template or boilerplate processes by cyber security teams. Lot of company is just doing it to check the boxes and they don’t really understanding what is to be done properly.
- Non-operational security posture. Inadequate tools and/or lack of proactive approach to mitigation. This means not being proactive as cyber security has to be a really part of this operations.
“so now I’ve spoken to you about problems, so I’m gonna give you a solutions. So simples thing that anybody can do here for your organization is to implement DMARC (domain-based Message Authentication, Reporting, and Conformance), DMARC is an effective tools so apply it.” Rohit Says.
Something more involved there is Drills raise awareness of social engineering attacks, a proper cyber awareness program.
Finally, more systemic measures. The most important is the adopt a risk based methodology for cyber security and this is give what might this look like.
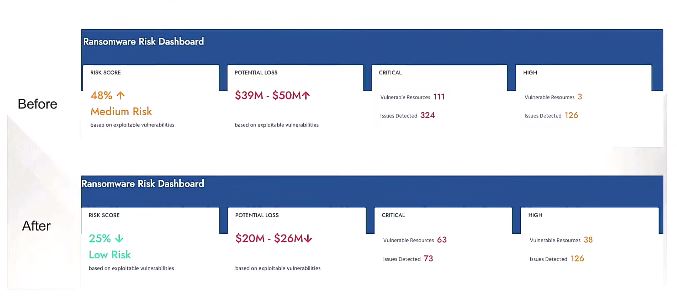
Rohid explained, this is an example of dashboard which we have develop for security people that join security business teams.
The potential for loss for your company has gone down from 50 Million dollars to 26 Million dollars. We collect data from all around the world and we know ransomware attacks how much the charged extra. so this risk based approached important because business people we’re management to see your management they understand this. They might not understand which packs to do deployed but they will understand the potential loss reduction in your organization.
Lastly, we have multi stage defense in depth programs is Policies, Procedures and Awareness; Physical; Perimeter; Internal Network; Host; App and Data. This means that you need to have not just one security posture but you have strong defense. And if you do all this things together that you can lower your cyber security. He closed.